Penetration Testing - pentest
Penetration testing to identify security risks
A penetration test is also called a pentest or a vulnerability analysis and is a ‘legal’ or ‘ethical hacker’ attack on a network, website, internet access or computer system. In advance, the owner of the system to be tested gives permission to certified and expert BSM pen testers to try to penetrate the system using computer programs and manual tests.
As a result, you will be able to see per risk to what extent it is a high risk, medium risk or low risk, so that you can resolve these vulnerabilities.
When the pen test succeeds in hacking the system, the builder or ict manager knows which weaknesses need to be improved and the owner of the system knows whether the system has just been securely built. For example, a pen test provides insight into the security risks and vulnerabilities of the computer system.
There are different types of pentests for the different types of systems and needs, which will be further explained below.
Which pen test is best for your situation?
Website scan
Website scan
A website scan is used to check simple websites, without interactive content and privacy-sensitive database, for weak spots that hackers can enter. A website scan is done partly automatically, by a computer program, and partly manually, by a white hat hacker of our company who identifies weak spots of the website in order to be ahead of real hackers. In this way common problems like cross-site scripting and defacement can be prevented.
Cross-site scripting means that hackers do not send text using entry fields such as contact forms. Instead, they send scripts that can do a lot of damage to your website, server or web environment. Defacement can be the result: hackers change the appearance of a website as a kind of digital graffiti.Unfortunately, this is often caused by a lack of knowledge, while the solution is often as simple as running a website scan.
For more information about website scans, we have created a specific page.
Pentesting on server and network
With a pentest on a server or network you can be ahead of the hacker and you keep the server for your own business. Did you know that on an average server thousands of hackers try to break in from outside every day?
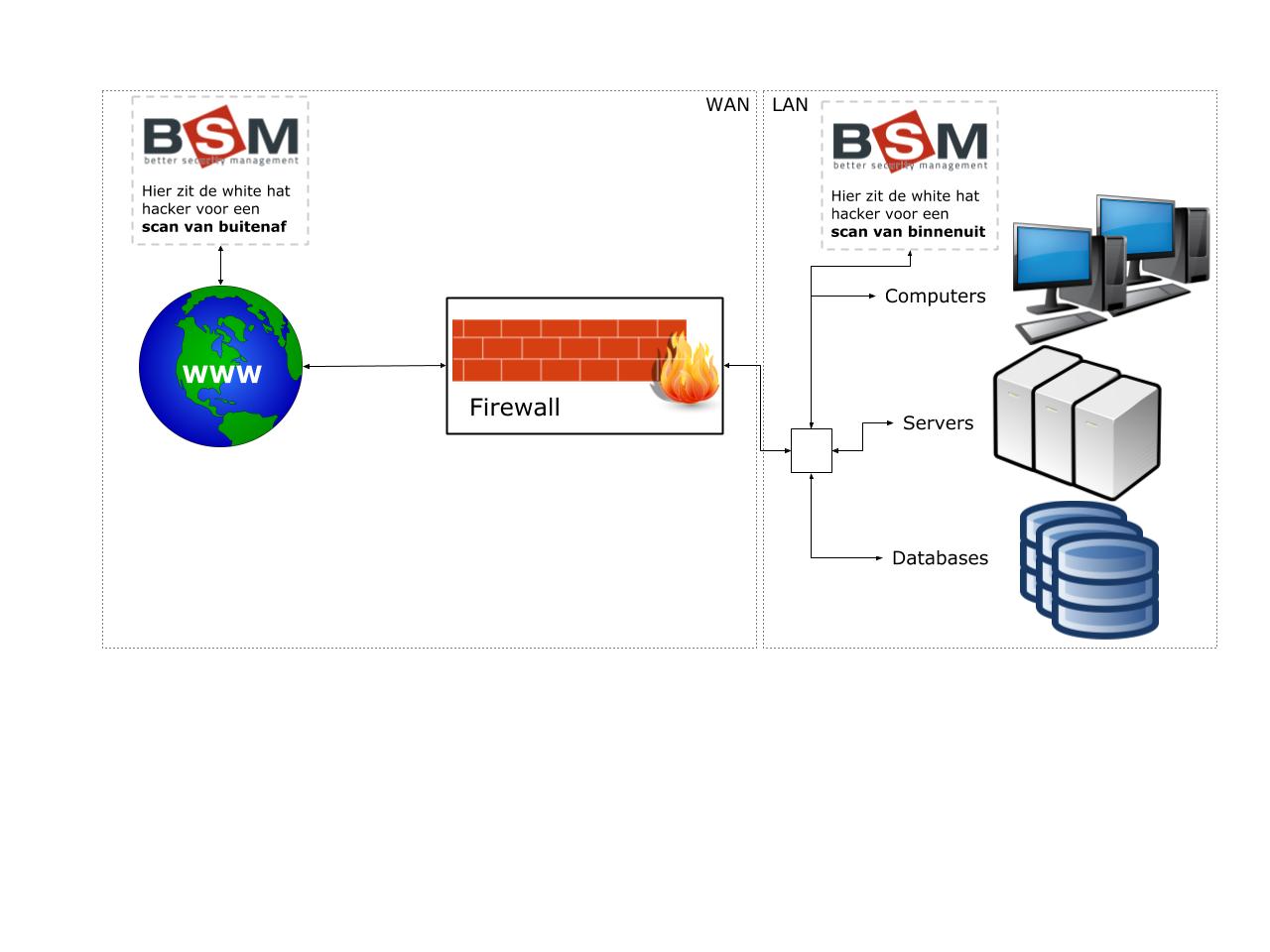
A company almost always has a network of computers, servers and databases. The network within the company is called the Local Area Network, abbreviated to LAN. This network is connected via a firewall to the World Wide Web, the Wide Area Network, abbreviated WAN. The task of the firewall is to try to intercept all unwanted traffic.
When a penetration test is conducted on the server and network, the security of the servers and other components of the network will be tested from the inside or the outside. This gives you information about vulnerabilities or security weaknesses in your network.
When we scan from the outside, this is done from another location through the internet. The scan then focuses on whether it is possible for hackers to break through the firewall in order to enter the LAN network and cause damage there.
For the scans from the inside, we look at what is possible when a hacker already has access to the LAN network, such as modifying databases or server functions or viewing data that should not be visible from certain computers. For such a scan, in most cases someone actually comes to the company with a laptop with the necessary software.
It is necessary to check your servers or network in these ways, because when a hacker takes over your server or network it can have serious consequences. For example, a hacker can take over websites, put sensitive information from databases on the street or use the servers for his own (possibly criminal) purposes that then happen in your name. It is also possible that an employee with malicious intent exploits the weaknesses in the LAN network.

Pentesting on applications
We advise you to have a pen test carried out on applications when customized software is used within your organization. Regularly custom software is not checked enough for security by software vendors. These tests are aimed at detecting weaknesses in your specific applications such as databases and content management systems. For this we use specialized software to scan the source codes of the software. In this way, we try to stay ahead of the hacker by finding out for ourselves which parts of the codes can be hacked. This gives you insight into which parts of your application need extra reinforcement.
These pentests are not only suitable if you use certain software, but also if you write software.
Active Monitoring And Pen Testing
BSM recommends active monitoring and pen testing when critical information, such as financial and privacy sensitive data, is present on the system. You must be able to prove that you have done everything in order to secure the data. You are required to do so by law in the case of sensitive data. With a pen test, you can prevent possible reputational and privacy damage and therefore also prevent damage claims from your employees, customers and suppliers.
With this scan we put ourselves in the role of a hacker and try to penetrate your network/ system in different ways. The scan is not performed by a computer program like many other scans. It is scanned by specialists who also try to perform less common hacks and they analyze the system based on important aspects for people. Examples include exploitation of human weaknesses (‘social engineering’) and depth attacks with tools such as the ‘metasploit framework’ (a platform of ICT security guards).
You will receive the result of the pentest in the form of a clear and usable report, with which you can put your supplier or ICT administrator to work. If necessary, BSM can also set out a course of action with steps to improve security and take care of the implementation of that plan.
Apply for a pentest
Would you like to apply for a penetration test? That is possible. With BSM's technical knowledge, we will work with you to ensure that you know where your weak spots are.
More about pen testing
There are several moments when a pen test can be useful:
In the acceptance phase of a new system or application;
In case of significant changes to an important system or application;
Periodically (annually/two years), to test existing systems for new burglary techniques;
read more
Method of pen testing
Would you like to know how BSM performs a penetration test? We have written out the steps in the penetration test process for you.
Contact with BSM
Would you like to have a consultation about the different types of pen tests and the possibilities? You can also contact us for more information.

