
Red Team vs Blue Team Exercise
Simulate a full-scale cyberattack to test your team’s incident response. BSM organizes red team attacks and supports blue team defense training.

Simulate a full-scale cyberattack to test your team’s incident response. BSM organizes red team attacks and supports blue team defense training.
Website Penetration Testing A website penetration test helps identify various types of security vulnerabilities in and around your website. In addition to scanning the site

Source Code Review A source code review—also known as a code-level penetration test—is a quality assessment of your software’s source code. This evaluation focuses not
Application Penetration Testing An application penetration test is a thorough security assessment of software and applications. It is intended for software developers as well as
LAN Penetration Test A LAN penetration test (LAN pentest) targets your internal network security. This includes your WiFi network and the connections between remote workstations
WAN Penetration Testing Almost every business today is connected to the internet.While this offers numerous advantages, it also presents serious risks if security is not
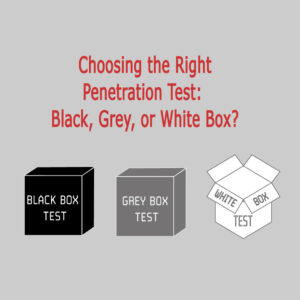
Compare Black Box, Grey Box, and White Box penetration testing methods. Determine the best fit for your organization’s cybersecurity needs with BSM’s expert guidance.

Penetration Testing Services Identify vulnerabilities before attackers do – discover BSM’s professional penetration testing services. Penetration testing—also known as pentesting, ethical hacking, or a vulnerability

A workstation audit provides crucial insights into the security status of your company’s workstations. We assess both the technical security and the behavior of users, giving you a complete picture of the risks within your organization.
What is Phishing? Phishing is a form of cybercrime in which a hacker impersonates a person or organization in order to persuade a victim to